In this article, you will learn how to configure the Active Directory Domain password policy.
The process of password synchronization involves components on the Active Directory domain controller and components on servers in the Domino domain. Password synchronization process flow Here are the steps that are taken to push a Windows user's new password in Active Directory to the HTTP password field in a Person document and to the Notes. Connect Azure Active Directory to the 1Password SCIM bridge. Learn how to set up and use the 1Password SCIM bridge to integrate with Azure Active Directory. Connect Okta to the 1Password SCIM bridge. Learn how to set up and use the 1Password SCIM bridge to integrate with Okta. Connect OneLogin to the 1Password SCIM bridge. Active Directory Integration – automate provisioning and de-provisioning. Okta Integration – allow Okta to manage your team for you. Command line Integration – integrate 1Password into your custom business flows. Now that we are starting to use Azure AD ourselves, onboarding those next 100 people should be a breeze.

You will also learn:
What is The Default Domain Password Policy?
By default, Active Directory is configured with a default domain password policy. This policy defines the password requirements for Active Directory user accounts such as password length, age and so on.

This password policy is configured by group policy and linked to the root of the domain. To view the password policy follow these steps: Download ptytrade port devices driver.
1. Open the group policy management console
2. Expand Domains, your domain, then group policy objects
3. Right click the default domain policy and click edit
4. Now navigate to Computer ConfigurationPoliciesWindows SettingsSecurity SettingsAccount PoliciesPassword Policy
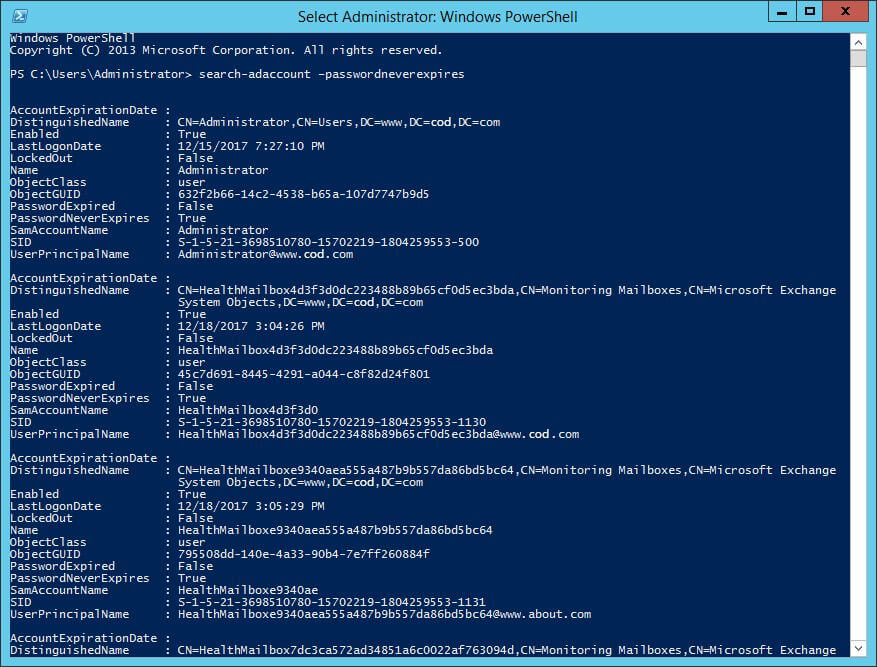
You can also view the default password policy with Powershell using this command.
Active Directory Password Requirement
Important: The default password policy is applied to all computers in the domain. If you want to apply different password policies to a group of users then it is best practice to use fine grained password policy. Do not create a new GPO and link it to an OU, this is not recommended.
Recommended Tool:Active Directory Cleanup Tool
Find inactive users and computers, keep AD secure and clean.
Understand Password Policy Settings
Now that you know how to view the domain default password policy lets look at the settings.
Enforce password history:
This setting defines how many unique passwords must be used before an old password can be reused. For example, if my current password is “Th334goore0!” then I can’t reuse that password until I’ve changed my password 24 times (or whatever number the policy is set to). This setting is useful so users don’t keep reusing the same password. The default setting is 24
Maximum password age:
This setting defines how long in days a password can be used before it needs to be changed. The default setting is 42 days
Minimum password age
This setting determines how long a password must be used before it can be changed. The default setting is 1 day
Minimum password length
This setting determines how many characters a password must have. The default is 7. This means my password must contain at least 7 characters.
Password must meet complexity requirements
If enabled passwords must meet these requirements:
- Not contain the user’s account name or parts of the user’s full name that exceed two consecutive characters
- Be at least six characters in length
- Contain characters from three of the following four categories:
- English uppercase characters (A through Z)
- English lowercase characters (a through z)
- Base 10 digits (0 through 9)
- Non-alphabetic characters (for example, !, $, #, %)
This is enabled by default
Store passwords using reversible encryption
This setting determines if the operating systems stores passwords using reversible encryption. This is essentially the same as storing plantest versions of passwords. This policy should NEVER be set to enabled unless you have some very specific application requirements. Noregon driver download.
Password Policy Best Practices
There are different opinions on this so I’m going to reference two sources. Also, your organization’s password policy may be driven by compliance/regulation requirements such as PCI/SOX/CJIS and so on.
Microsofts recommended password settings
These settings are from Microsoft’s Security Compiance Toolkit. This toolkit provides recommended GPO settings from Microsoft.
- Enforce Password History: 24
- Maximum password age: not set
- Minimum password age: not set
- Minimum password length: 14
- Password must meet complexity: Enabled
- Store passwords using reversible encryption: Disabled
NOTE: Microsoft has dropped the password expiration policies starting with the 1903 security baseline. You can read more on this here
I think this is a good decision but some organizations will still need to follow specific guides (like PCI, SOX, CJIS). Hopefully, those will get updated soon.
CIS Benchmark password settings
These settings are from the CIS Benchmarks. The center for internet security is a non for profit organization that develops security guidelines and benchmarks.
- Enforce Password History: 24
- Maximum password age: 60 or fewer days
- Minimum password age: 1 or more
- Minimum password length: 14
- Password must meet complexity: Enabled
- Store passwords using reversible encryption: Disabled
Modify Default Domain Password Policy
1password Active Directory
To modify the password policy you will need to modify the default domain policy.
1. Open the group policy management console
2. Expand Domains, your domain, then group policy objects
3. Right click the default domain policy and click edit
4. Now navigate to Computer ConfigurationPoliciesWindows SettingsSecurity SettingsAccount PoliciesPassword Policy
5. Now double click one of the settings to edit. For example, I’ll double chick on minimum password length.
I’m going to change this setting from 7 to 14 character and then click apply.
Double click any other password policy setting to change.
I hope you enjoyed this article.
Do you have any questions? Let me know in the comments below.
Recommended Tool: SolarWinds Server & Application Monitor
This utility was designed to Monitor Active Directory and other critical services like DNS & DHCP. It will quickly spot domain controller issues, prevent replication failures, track failed logon attempts and much more.
Active Directory Password Cracking
What I like best about SAM is it’s easy to use dashboard and alerting features. It also has the ability to monitor virtual machines and storage.
